On 20 July, Microsoft had released a report on the latest edition of its Security Endpoint Threat Report 2019 and one of the press releases had focused on its Asia Pacific findings.
Malware and ransomware attacks
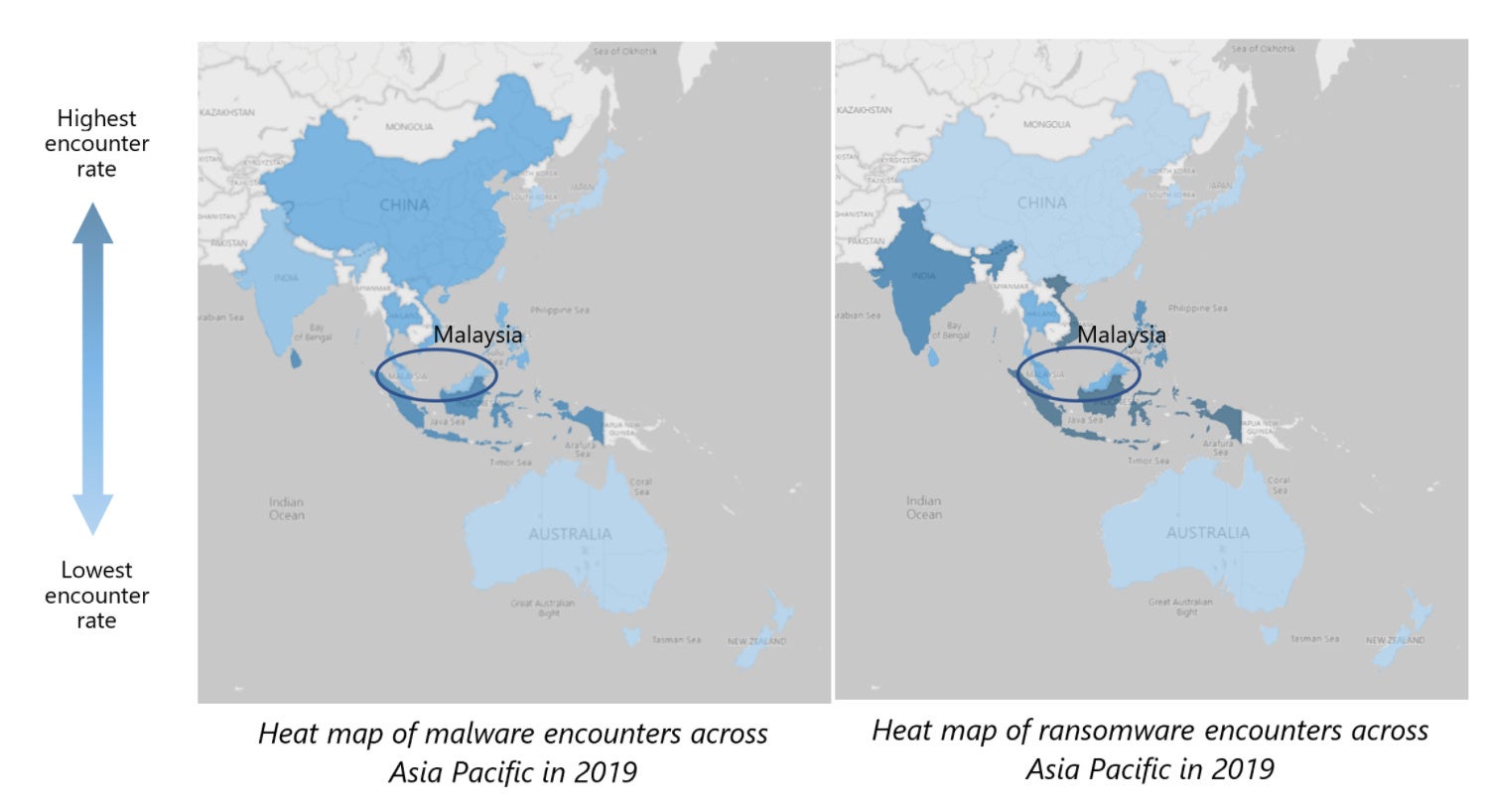
Apparently, there was a decrease in cyberthreat encounters in Malaysia, across cryptocurrency mining, malware and ransomware encounters and drive-by download attacks in 2019.
Malaysia’s malware encounter was reported to have decreased by 36% and achieved 4.81%, therefore making Malaysia the 8th highest encounter rate across the region and 1.1 times lower than the regional average.
According to Microsoft, Asia Pacific continues to experience a higher-than-average encounter rate for malware and ransomware attacks, and it was about 1.6 and 1.7 times higher than the rest of the world respectively.
The Chief Executive Officer of CyberSecurity Malaysia, Dato’ Ts Dr Haji Amirudin Bin Abdul Wahab, mentioned that although the number of encounters was reduced, cyberattacks are still a serious threat to organisations in Malaysia.
“Despite a reduction in the number of encounters, cyberattacks remain a serious threat to organisations across Malaysia.”
Other than that, the majority of Malaysians were made to shift to remote working during the Movement Control Order, thus, many organisations began to take cybersecurity “very seriously”.
“With the announcement of the Movement Control Order (MCO) in March, we saw a shift to remote working, leveraging technology to sustain business continuity. This shift simultaneously demands attention to cybersecurity, which many organisations have taken very seriously.
The Security Endpoint Threat report findings provide valuable insight and understanding for organisations to leverage as they continue to work in a digital environment moving forward.”
Cryptocurrency mining in Malaysia
As for cryptocurrency mining encounter rate, Microsoft revealed that Malaysia recorded a 69% decrease, from 0.16 in 2018 to 0.05 in 2019. This encounter rate is the 7th highest across the region, and it is also on par with both the regional and global average.
Microsoft explained that during cryptocurrency attacks, victims’ computers would be infected with cryptocurrency mining malware that would allow criminals to “leverage the computing power of their computers” without the victims’ knowledge.
Drive-by download attack volume in Malaysia
Malaysia managed to record a “significant decrease” in the drive-by download attack volume, which was a whopping 93%, achieving 0.04 in 2019. This volume was the 9th highest across the region, and it was also two times lower than the regional and global average.
The National Technology Officer of Microsoft Malaysia, Dr Dzahar Mansor, explained that drive-by download attacks were usually launched by cybercriminals to steal financial information or intellectual property. He had also expressed that having a “high attack volume” doesn’t mean there’s a “high infection rate”, but rather it was thanks to the organisations’ good cyber hygiene practices.
“We usually see cybercriminals launch such attacks to steal financial information or intellectual property. This is a likely reason why regional financial hubs recorded the highest volume of such threats. The high attack volume in these markets may not necessarily translate into a high infection rate, perhaps due to their good cyber hygiene practices and use of genuine software.”
To protect yourselves from these malicious attacks, Microsoft provided two sets of guidelines for businesses and individuals.
Guidance for businesses:
- Have strong tools to safeguard employees and infrastructure. This means looking into multi-layered defence systems and turning on multi-factor authentication (MFA) as employees work from home. Additionally, enable endpoint protection and protect against shadow IT and unsanctioned app usage with solutions like Microsoft Cloud App Security.
- Ensure employee guidelines are communicated clearly to employees. This includes information on how to identify phishing attempts, distinguishing between official communications and suspicious messages that violate company policy, and where these can be reported internally.
- Choose a trusted application for audio/video calling and file-sharing that ensures end-to-end encryption.
Guidance for individuals:
- Update all devices with the latest security updates and use an antivirus or anti-malware service. For Windows 10 devices, Microsoft Defender Antivirus is a free built-in service enabled through settings.
- Be alert to links and attachments, especially from unknown senders.
- Use multi-factor authentication (MFA) on all accounts. Now, most online services provide a way to use your mobile device or other methods to protect your accounts in this way.
- Get educated on how to recognize phishing attempts and report suspected encounters, including watching out for spelling and bad grammar, and suspicious links and attachments from people you do not know.
Also read: Gobind Singh: New Cybersecurity Policy to Be Introduced in 2019 to Curb Cyberattacks









































